Olá,
Neste tutorial iremos criar um tunnel de VPN entra Azure (RoutedBased) e Palo Alto (Iremos abordar somente configuração do no Palo Alto).
Iremos considerar o seguinte cenário:
Rede Local (Palo Alto): 10.91.0.0/16
Rede Remota (Azure): 10.255.0.0/16
https://docs.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-about-vpn-devices
No Palo Alto
1-) Passo
 IKE Crypto
IKE Crypto
Name: ike_crypto_azure
DH Group: group2
Encryption: aes-128-cbc
Authentication: sha1
Key Lifetime: Seconds 29000
IKEv2 Authentication Multiple: 0
2) Passo
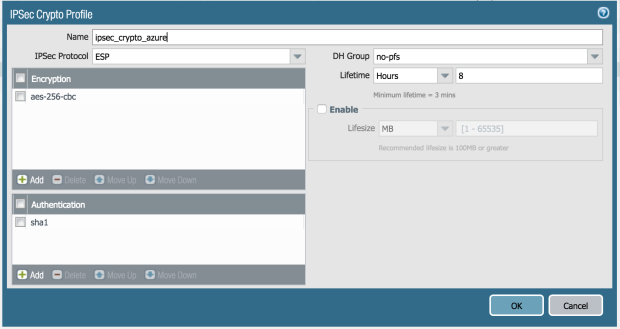
IPSec Crypto
Name: ipsec_crypt_azure
Encryption: aes-256-cbc
Authentication: sha1
DH Group: no-pfs
Lifetime: Hours 8
3) Passo
 IKE Gateway (General)
IKE Gateway (General)
Name: ike_gateway_azure
Version: IKEv2 only mode
Address Type: IPv4
Interface: ae1.200 (Neste exemplo essa é minha interface)
Peer IP Type: Static
Peer IP Address: IP do PUBLICO
Pre-shared Key: XXXXXXXXXXXX
Local Identification: Nome
Local Identification: Nome
4) Passo
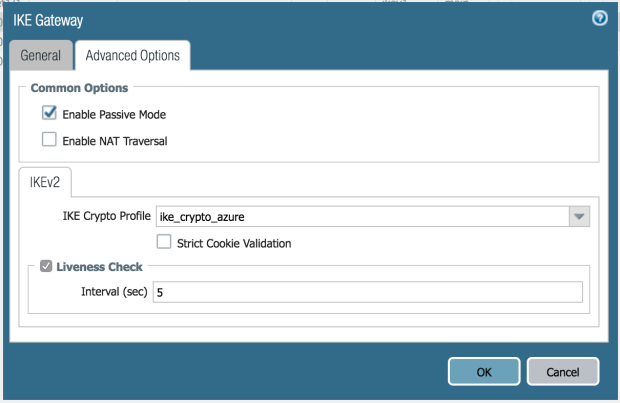
IKE Gateway (Advanced Options)
Common Options: Enable Passive Mode
IKEv2: ike_crypt_azure
Liveness Check: Interval (sec) 5
5) Passo
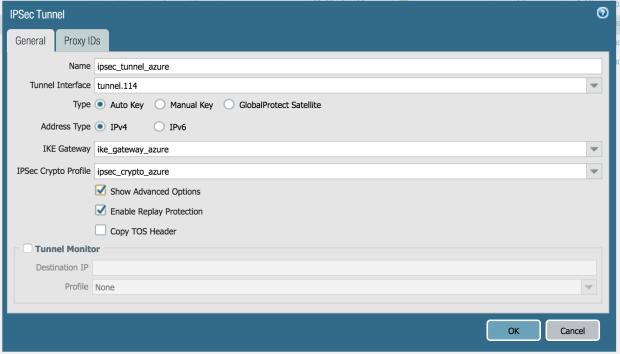
Interfaces
Add
Name: ipesec_tunnel_azure
Tunnel Interface: tunnel.114
Type: Auto Key
Address Typer: IPv4
IKE Gateway: ike_gateway_azure
IPSec Crypto Profile: ipsec_crypt_azure
Show Advanced Options
Enable Replay Protection
6) Passo
Proxy ID
 Sem Proxy ID
Sem Proxy ID
Pronto!!! Tunel de VPN entre Palo Alto e Azure está ok.
Não esqueça de criar:
Route – Zone – Rule Firewall












Você precisa fazer login para comentar.