Neste post vamos criar uma infraestrutura no Azure utilizando Azure Firewall.
Teremos o Azure Firewall em nossa Borda (EDGE), neste exemplo a rota Default “0.0.0.0/0” (Para internet) passará obrigatoriamente pelo Azure Firewall, com isso qualquer serviços que estiver anexado a snet que com a rota para o Azure Firewall terá que possuir regras de OutBound para poder acessar a internet. Vamos lá!!!!

Vamos aos nossos objetos:
Neste exemplo teremos:
Resource Group “rt-sec-fwedge-shared-eastus”
Public IP “pip-mgt-sec-fwedge-shared-eastus”
Public IP “pip-sec-fwedge-shared-eastus”
Route Table “rt-sec-fwedge-shared-eastus”
Vnet “vnet-sec-fwedge-shared-eastus”
Snet “AzureFirewallSubnet”
Snet “AzureFirewallManagementSubnet”
Snet “Snet-Protected”

Vamos ao nosso código (Shell)
#!/bin/bash
##Declarando Variaveis (Obrigatório)
export Subscription_Name="XXXXXXXXXXXXXXX" ##Substituir pela sua Subscription
export RG="rg"
export Depto="sec"
export Object_Name="fwedge"
export Env="shared"
export Location="eastus"
export RGName="${RG}"-"${Depto}"-"${Object_Name}"-"${Env}"-"${Location}"
##Declarando Variaveis Vnet/Snet
export Vnet="vnet"
export CIDR="10.128.1.0/24"
export VNetName="${Vnet}"-"${Depto}"-"${Object_Name}"-"${Env}"-"${Location}"
##Variaveis de Snet
export Snet="snet"
export SubnetName01="AzureFirewallSubnet"
export SubnetName02="AzureFirewallManagementSubnet"
export SubnetName03="Snet-Protected"
export Prefix01_01="10.128.1.0/26"
export Prefix01_02="10.128.1.64/26"
export Prefix01_03="10.128.1.128/26"
##Declarando Variaveis SKU/TIER
export SKU="AZFW_VNet"
export TIER="Standard"
##Declarando Variaveis de IPs Publicos
export PublicIP_Object="pip"
export NameIP_Config="ifconfig"
export Config_IP01="1"
export Config_IP02="2"
export SKU_IP="Standard"
export AlLocation="Static"
export Tier_IP="Regional"
export PublicIP_Name="${PublicIP_Object}"-"${Depto}"-"${Object_Name}"-"${Env}"-"${Location}"
export PublicIP_NameMGT="${PublicIP_Object}"-"mgt"-"${Depto}"-"${Object_Name}"-"${Env}"-"${Location}"
##Declarando variaveis de ZONA
export Zone="1"
##Variaveis do Firewall
export Tier_FW="Standard"
export Threat="Alert"
export SKU_FW="AZFW_VNet"
export FWName_Object="fw"
export FWName="${FWName_Object}"-"${Depto}"-"${Object_Name}"-"${Env}"-"${Location}"
##Variaveis de Route Table
export RTName_Object="rt"
export RTName="${RTName_Object}"-"${Depto}"-"${Object_Name}"-"${Env}"-"${Location}"
export RouteName="Default"
export RT_Prefix="0.0.0.0/0"
##Variaveis de Rules/Colletion (Firewall)
export Colletion_Name_Internet="AcessoInternet"
##Variaveis de Tags
export Description="Departamento"
export Value_Description="${Depto}"
export Cost_Center="Centro de Custo"
export Cost_Center_Value="${Depto}"
export Support_Description_Description="E-mail Suporte"
export Support_Description_Value="[email protected]"
###Selecionar subscription
az account set --subscription "${Subscription_Name}"
##Criando RG
az group create -n "${RGName}" -l "${Location}" --tags "${Description}"="${Value_Description}" "${Cost_Center}"="${Cost_Center_Value}" "${Support_Description_Description}"="${Support_Description_Value}"
##Criando Vnet
az network vnet create -g "${RGName}" -n "${VNetName}" --address-prefix "${CIDR}" -l "${Location}" --tags "${Description}"="${Value_Description}" "${Cost_Center}"="${Cost_Center_Value}" "${Support_Description_Description}"="${Support_Description_Value}"
##Criando Snet
az network vnet subnet create -g "${RGName}" --vnet-name "${VNetName}" -n "${SubnetName01}" --address-prefixes "${Prefix01_01}"
az network vnet subnet create -g "${RGName}" --vnet-name "${VNetName}" -n "${SubnetName02}" --address-prefixes "${Prefix01_02}"
az network vnet subnet create -g "${RGName}" --vnet-name "${VNetName}" -n "${SubnetName03}" --address-prefixes "${Prefix01_03}"
##Criando IP Publico
az network public-ip create -g "${RGName}" -n "${PublicIP_Name}" -l "${Location}" --zone "${Zone}" --allocation-method "${AlLocation}" --sku "${SKU_IP}" --tier "${Tier_IP}" --tags "${Description}"="${Value_Description}" "${Cost_Center}"="${Cost_Center_Value}" "${Support_Description_Description}"="${Support_Description_Value}"
az network public-ip create -g "${RGName}" -n "${PublicIP_NameMGT}" -l "${Location}" --zone "${Zone}" --allocation-method "${AlLocation}" --sku "${SKU_IP}" --tier "${Tier_IP}" --tags "${Description}"="${Value_Description}" "${Cost_Center}"="${Cost_Center_Value}" "${Support_Description_Description}"="${Support_Description_Value}"
##Criando Azure Firewall
az network firewall create -g "${RGName}" -n "${FWName}" --sku "${SKU_FW}" --tier "${Tier_FW}" -z "${Zone}" --threat-intel-mode "${Threat}" --tags "${Description}"="${Value_Description}" "${Cost_Center}"="${Cost_Center_Value}" "${Support_Description_Description}"="${Support_Description_Value}"
##Associando IP Publico Azure Firewall
az network firewall ip-config create -g "${RGName}" -f "${FWName}" -n "${NameIP_Config}"-"${Config_IP01}" --public-ip-address "${PublicIP_Name}" --vnet-name "${VNetName}" --m-name "${NameIP_Config}"-"${Config_IP02}" --m-public-ip-address "${PublicIP_NameMGT}" --m-vnet-name "${VNetName}"
az network firewall ip-config create -g "${RGName}" -f "${FWName}" --m-name "${NameIP_Config}"-"${Config_IP02}" --m-public-ip-address "${PublicIP_NameMGT}" --m-vnet-name "${VNetName}"
##Update Firewall
az network firewall update -g "${RGName}" -n "${FWName}"
###Declarando Variaveis para utilizar IP privado do Azure Firewall
export fwprivaddr="$(az network firewall ip-config list -g "${RGName}" -f "${FWName}" --query "[?name=='ifconfig-1'].privateIpAddress" --output tsv)"
###Crando Route Table
az network route-table create -g "${RGName}" -n "${RTName}" -l "${Location}" --disable-bgp-route-propagation "true"
###Associando Route Table a Subnet
az network vnet subnet update -g "${RGName}" -n "${SubnetName03}" --vnet-name "${VNetName}" --address-prefixes "${Prefix01_03}" --route-table "${RTName}"
az network vnet subnet update -g "${RGName}" -n "${SubnetName01}" --vnet-name "${VNetName}" --address-prefixes "${Prefix01_02}" --route-table "${RTName}"
###Criando Static Route
az network route-table route create -g "${RGName}" --name "${RouteName}" --route-table-name "${RTName}" --address-prefix "${RT_Prefix}" --next-hop-type "VirtualAppliance" --next-hop-ip-address "${fwprivaddr}"
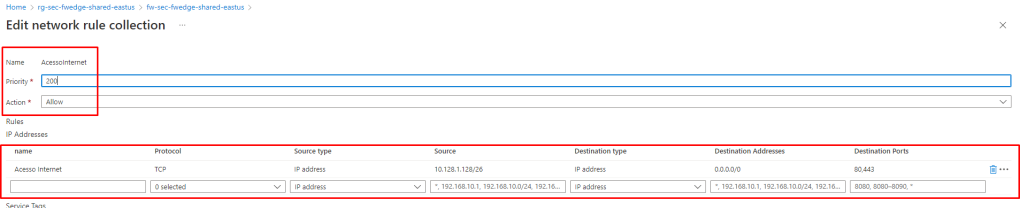
###Criando Regras de acesso para Internet (somente HTTP/HTTPs)
az network firewall network-rule create -c "${Colletion_Name_Internet}" \
--destination-ports "80" "443" -f "${FWName}" -n "Acesso Internet" \
--protocols "TCP" -g "${RGName}" --action "Allow" \
--description "Internet Access Network Protected" --dest-addr "0.0.0.0/0" \
--priority "200" --source-addresses "${Prefix01_03}" Após execução do Shell acima, além dos objetos criados, as VMs que estiverem na rede Snet-Protected teram acesso a internet, pois foi criado uma Rule Network para este fim.
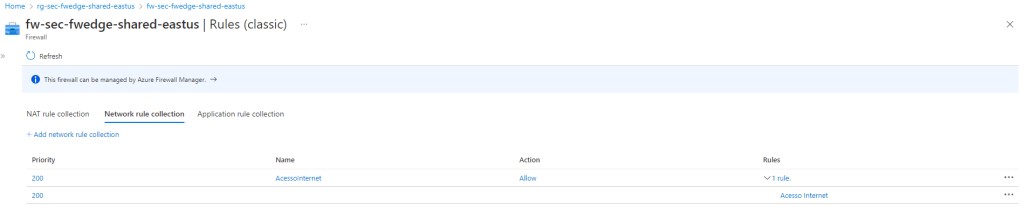
*Obs, é possivel criar regras de InBound (NAT) para acessar um serviços dentro de uma VM que esta atrás do Azure Firewall. Consulte neste Post
Links de Referencias:
https://docs.microsoft.com/en-us/cli/azure/network/firewall?view=azure-cli-latest
https://docs.microsoft.com/en-us/azure/firewall/deploy-cli
https://docs.microsoft.com/en-us/cli/azure/network/firewall/network-rule?view=azure-cli-latest
https://docs.microsoft.com/en-us/cli/azure/network/firewall/policy?view=azure-cli-latest
https://docs.microsoft.com/en-us/cli/azure/network/firewall/application-rule?view=azure-cli-latest
https://docs.microsoft.com/en-us/cli/azure/network/firewall/ip-config?view=azure-cli-latest#az-network-firewall-ip-config-list






Você precisa fazer login para comentar.