Neste post iremos demonstrar o deploy de Virtuais Machines em Windows Server 2016 com IIS Habilitado, porém iremos fazer em alta disponibilidade com metade de nosso ambiente em ZONA 1 e a outra metade em ZONE 2, a diferença aqui será no deploy feito com @Array, com isso conseguimos criar varias VMs em apenas uma linha de comando azure cli bash.
Vamos ao nosso cenário:

Vamos ao nosso código bash (azure cli)
##Declarando Variaveis (Obrigatório)
export Subscription_Name="XXXXXXXXXXXXX" ###Substituir pela sua subscription
export RG="rg"
export Depto_Corp="corp"
export ObjectNameCorp="web"
export Env="prod"
export Location="eastus"
export RGNameCorpWeb="${RG}"-"${Depto_Corp}"-"${ObjectNameCorp}"-"${Env}"-"${Location}"
##Declarando Variaveis de Rede
export vnet="vnet"
export VnetNameWEB="${vnet}"-"${Depto_Corp}"-"${ObjectNameCorp}"-"${Env}"-"${Location}"
export CIDR_WEB="10.40.50.0/24"
export Prefix_WEBFE01="10.40.50.0/26"
export Prefix_WEBFE02="10.40.50.64/26"
export snet="snet"
export SnetNameWebFE01="${snet}"-"${Depto_Corp}"-"${ObjectNameCorp}"-"${Env}"-"${Location}"-fe01
export SnetNameWebFE02="${snet}"-"${Depto_Corp}"-"${ObjectNameCorp}"-"${Env}"-"${Location}"-fe02
##Declarando Variaveis de VMs
export VM_Object_Name="vm"
export VMName="${VM_Object_Name}""${ObjectNameCorp}""${Env}"
export SKU="Standard_LRS"
export Image_Windows="Win2016Datacenter"
export OsDisk_Name="disk-os"
export Zone01="1"
export Zone02="2"
export UserName="azroot"
export Password="WelCome_Az@#"
export VMSize="Standard_DS1_v2"
##Declarando Variaveis de Interfaces de Rede
export Int_Object_Name01="int"
export Int_Object_Name02="eth"
export Int_Number="0"
export IntNameWeb="${Int_Object_Name01}"-"${Int_Object_Name02}""${Int_Number}"-"${VM_Object_Name}"-"${ObjectNameCorp}"-"${Location}"
##Declarando Variaveis de Storage Account
export Storage_Object_Name01="stg"
export Storage_Object_Name02="diag"
export StorageNameFE="${Storage_Object_Name01}""${Storage_Object_Name02}""${VM_Object_Name}""${ObjectNameCorp}""${Depto_Corp}"
##Declarando Variaveis NSG
export NSG_Object_Name="nsg"
export NSGWEB="${NSG_Object_Name}"-"${snet}"-"${Depto_Corp}"-"${Env}"-"${Location}"-fe
##Variaveis de Load Balance
export ObjectNameWebLB="lb"
export ObjectName_WebLB="${ObjectNameWebLB}"-"${Depto_Corp}"-"${ObjectNameCorp}"-"${Env}"-"${Location}"
export SKULB="Standard"
export PoolFE="PoolFE"
export PoolBE="PoolBackend"
##Declarando Variaveis de IP Publico
export PublicIPWebObject="pip"
export PublicIPWebSku="Standard"
export PublicIPNameWeb01="${PublicIPWebObject}"-"${Depto_Corp}"-"${ObjectNameCorp}"-"${Env}"-"${Location}"-1
##Variaveis de Tags
export Description="Departamento"
export Value_Description="${Depto_Corp}"
export Cost_Center="Centro de Custo"
export Cost_Center_Value="${Depto_Corp}"
export Support_Description_Description="E-mail Suporte"
export Support_Description_Value="support"-"${Depto_Corp}""@xpto.com"
###Selecionar subscription
az account set --subscription "${Subscription_Name}"
###Criando Resource Group
az group create -n "${RGNameCorpWeb}" -l "${Location}" \
--tags "${Description}"="${Value_Description}" "${Cost_Center}"="${Cost_Center_Value}" "${Support_Description_Description}"="${Support_Description_Value}"
###Criando Storage Account
az storage account create -g "${RGNameCorpWeb}" -n "${StorageNameFE}" --sku "${SKU}" -l "${Location}" --tags "${Description}"="${Value_Description}" "${Cost_Center}"="${Cost_Center_Value}" "${Support_Description_Description}"="${Support_Description_Value}"
###Criando NSG
az network nsg create -g "${RGNameCorpWeb}" -n "${NSGWEB}" -l "${Location}" \
--tags "${Description}"="${Value_Description}" "${Cost_Center}"="${Cost_Center_Value}" "${Support_Description_Description}"="${Support_Description_Value}"
###Criando Regras NSG InBound
az network nsg rule create -g "${RGNameCorpWeb}" --nsg-name "${NSGWEB}" --name 'AllowHttpsInBound' \
--protocol 'tcp' --direction 'inbound' --source-address-prefix 'internet' --source-port-range '*' \
--destination-address-prefix '*' --destination-port-range '443' --access 'Allow' --priority '120'
az network nsg rule create -g "${RGNameCorpWeb}" --nsg-name "${NSGWEB}" --name 'AllowHttpInBound' \
--protocol 'tcp' --direction 'inbound' --source-address-prefix 'internet' --source-port-range '*' \
--destination-address-prefix '*' --destination-port-range '80' --access 'Allow' --priority '121'
###Criando Vnet
az network vnet create -g "${RGNameCorpWeb}" -n "${VnetNameWEB}" --address-prefix "${CIDR_WEB}" \
-l "${Location}" --tags "${Description}"="${Value_Description}" "${Cost_Center}"="${Cost_Center_Value}" "${Support_Description_Description}"="${Support_Description_Value}"
###Criando Snet
az network vnet subnet create -g "${RGNameCorpWeb}" --vnet-name "${VnetNameWEB}" \
-n "${SnetNameWebFE01}" --address-prefixes "${Prefix_WEBFE01}"
az network vnet subnet create -g "${RGNameCorpWeb}" --vnet-name "${VnetNameWEB}" \
-n "${SnetNameWebFE02}" --address-prefixes "${Prefix_WEBFE02}"
###Anexando NSG a Snet
az network vnet subnet update -g "${RGNameCorpWeb}" --vnet-name "${VnetNameWEB}" \
-n "${SnetNameWebFE01}" --network-security-group "${NSGWEB}"
az network vnet subnet update -g "${RGNameCorpWeb}" --vnet-name "${VnetNameWEB}" \
-n "${SnetNameWebFE02}" --network-security-group "${NSGWEB}"
###Criando IP Publico
az network public-ip create -g "${RGNameCorpWeb}" -n "${PublicIPNameWeb01}" --sku "${PublicIPWebSku}"
##Criando interfaces de Rede (Snet1)
array=("${IntNameWeb}"-001 "${IntNameWeb}"-002 "${IntNameWeb}"-003 "${IntNameWeb}"-004 "${IntNameWeb}"-005)
for vmnic in "${array[@]}"
do
az network nic create \
--resource-group "${RGNameCorpWeb}" --name $vmnic --vnet-name "${VnetNameWEB}" --subnet "${SnetNameWebFE01}"
done
##Criando interfaces de Rede (Snet2)
array=("${IntNameWeb}"-006 "${IntNameWeb}"-007 "${IntNameWeb}"-008 "${IntNameWeb}"-009 "${IntNameWeb}"-010)
for vmnic in "${array[@]}"
do
az network nic create \
--resource-group "${RGNameCorpWeb}" --name $vmnic --vnet-name "${VnetNameWEB}" --subnet "${SnetNameWebFE02}"
done
###Criando Maquinas Virtuais
array=(-001 -002 -003 -004 -005)
for n in "${array[@]}"
do
az vm create -g "${RGNameCorpWeb}" --name "${VMName}"$n --nics "${IntNameWeb}"$n \
--image "${Image_Windows}" \
--admin-username "${UserName}" \
--admin-password "${Password}" \
--os-disk-name "${OsDisk_Name}"-"${VMName}"$n \
--zone "1" --size "${VMSize}" \
--boot-diagnostics-storage "${StorageNameFE}" \
--tags "${Description}"="${Value_Description}" "${Cost_Center}"="${Cost_Center_Value}" "${Support_Description_Description}"="${Support_Description_Value}"
done
array=(-006 -007 -008 -009 -010)
for n in "${array[@]}"
do
az vm create -g "${RGNameCorpWeb}" --name "${VMName}"$n --nics "${IntNameWeb}"$n \
--image "${Image_Windows}" \
--admin-username "${UserName}" \
--admin-password "${Password}" \
--os-disk-name "${OsDisk_Name}"-"${VMName}"$n \
--zone "2" --size "${VMSize}" \
--boot-diagnostics-storage "${StorageNameFE}" \
--tags "${Description}"="${Value_Description}" "${Cost_Center}"="${Cost_Center_Value}" "${Support_Description_Description}"="${Support_Description_Value}"
done
###Ativando IIS nas VMs criadas
array=(-001 -002 -003 -004 -005 -006 -007 -008 -009 -010)
for n in "${array[@]}"
do
az vm extension set --publisher Microsoft.Compute --version 1.8 --name CustomScriptExtension \
--vm-name "${VMName}"$n --resource-group "${RGNameCorpWeb}" \
--settings '{"commandToExecute":"powershell Install-WindowsFeature -Name Web-Server -IncludeAllSubFeature -IncludeManagementTools; powershell Add-Content -Path \"C:\\inetpub\\wwwroot\\Default.htm\" -Value $($env:computername)"}'
done
##Criando Load Balance
az network lb create -g "${RGNameCorpWeb}" -n "${ObjectName_WebLB}" --sku "${SKULB}" \
--frontend-ip-name "${PoolFE}" --backend-pool-name "${PoolBE}" --public-ip-address "${PublicIPNameWeb01}" \
--tags "${Description}"="${Value_Description}" "${Cost_Center}"="${Cost_Center_Value}" "${Support_Description_Description}"="${Support_Description_Value}"
#Create health probe on port 80/443
az network lb probe create -g "${RGNameCorpWeb}" --lb-name "${ObjectName_WebLB}" \
--name "Probe-HTTPS" --protocol tcp --port 443
az network lb probe create -g "${RGNameCorpWeb}" --lb-name "${ObjectName_WebLB}" \
--name "Probe-HTTP" --protocol tcp --port 80
#Create load balancer rule for port 80/443
az network lb rule create -g "${RGNameCorpWeb}" --lb-name "${ObjectName_WebLB}" \
--name "HTTP" --protocol "tcp" --frontend-port 80 --backend-port 80 --frontend-ip-name "${PoolFE}" \
--backend-pool-name "${PoolBE}" --probe-name Probe-HTTP
az network lb rule create -g "${RGNameCorpWeb}" --lb-name "${ObjectName_WebLB}" \
--name "HTTPS" --protocol "tcp" --frontend-port 443 --backend-port 443 --frontend-ip-name "${PoolFE}"
--backend-pool-name "${PoolBE}" --probe-name Probe-HTTPS
#Adicionando Inteface REDE ao pool de backend Load Balance
array=("${IntNameWeb}"-001 "${IntNameWeb}"-002 "${IntNameWeb}"-003 "${IntNameWeb}"-004 "${IntNameWeb}"-005 "${IntNameWeb}"-006 "${IntNameWeb}"-007 "${IntNameWeb}"-008 "${IntNameWeb}"-009 "${IntNameWeb}"-010)
for vmnic in "${array[@]}"
do
az network nic ip-config address-pool add \
--resource-group "${RGNameCorpWeb}" \
--nic-name $vmnic \
--address-pool "${PoolBE}" \
--ip-config-name "ipconfig1" \
--lb-name "${ObjectName_WebLB}"
done
####Fim do ScriptVamos aos objetos criados
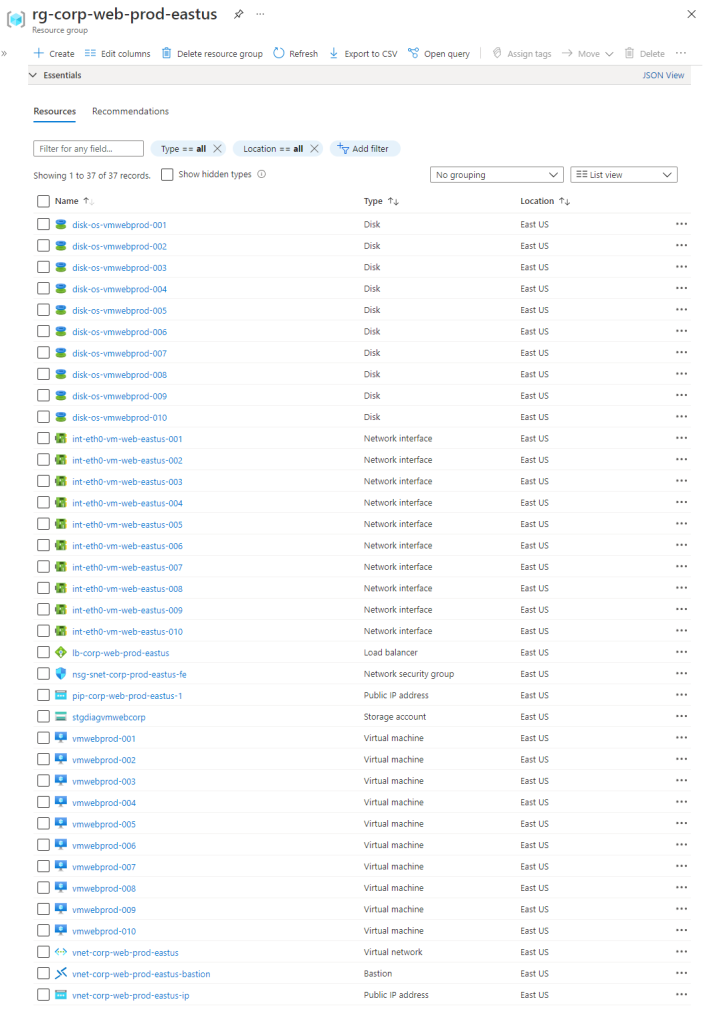
Nossas VM em Zonas diferentes ###
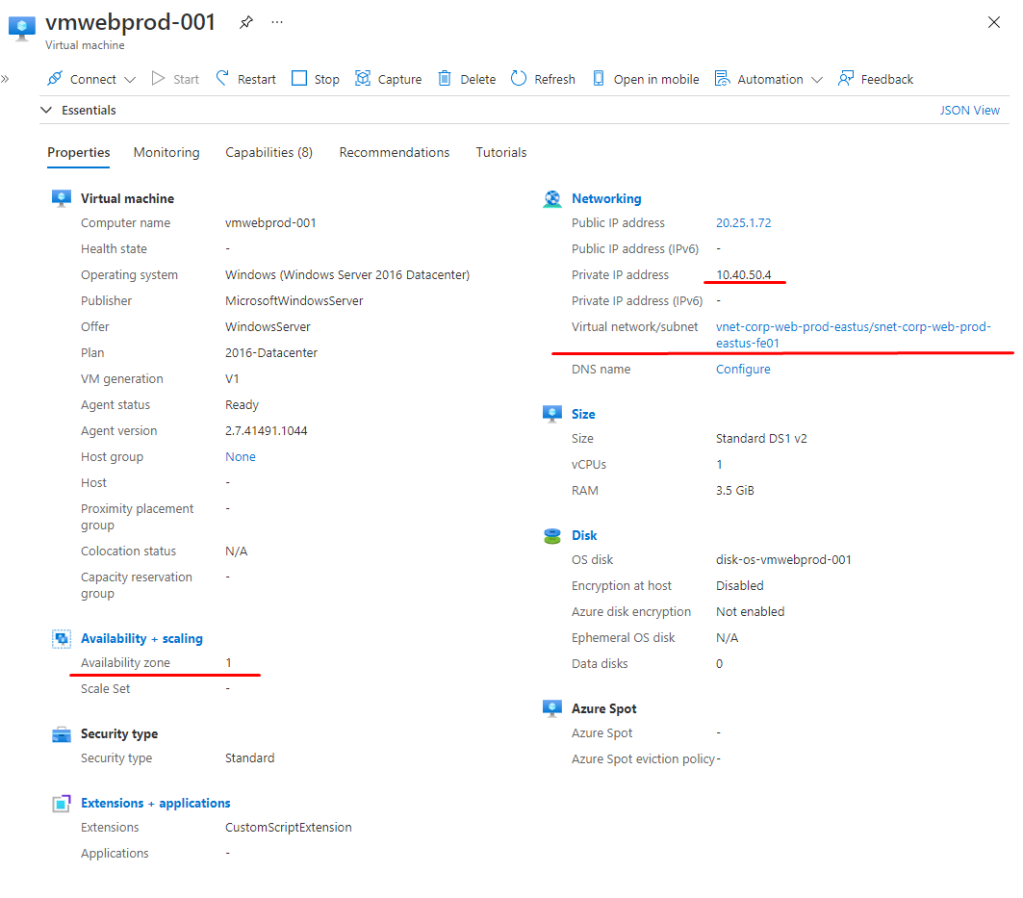

Nosso LB



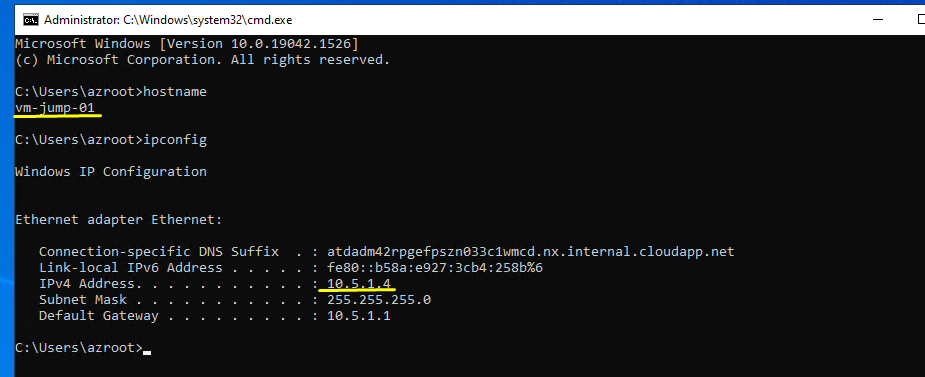
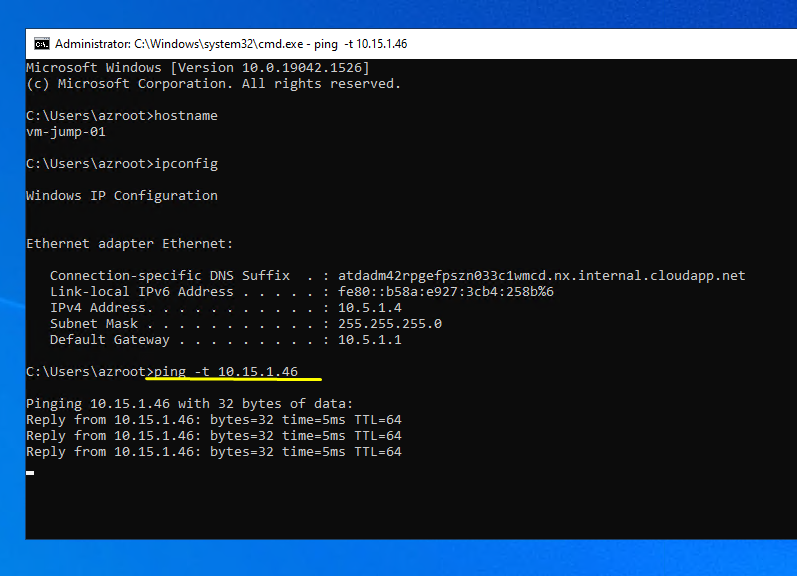
Vamos ver nossoas VM com ISS instalado
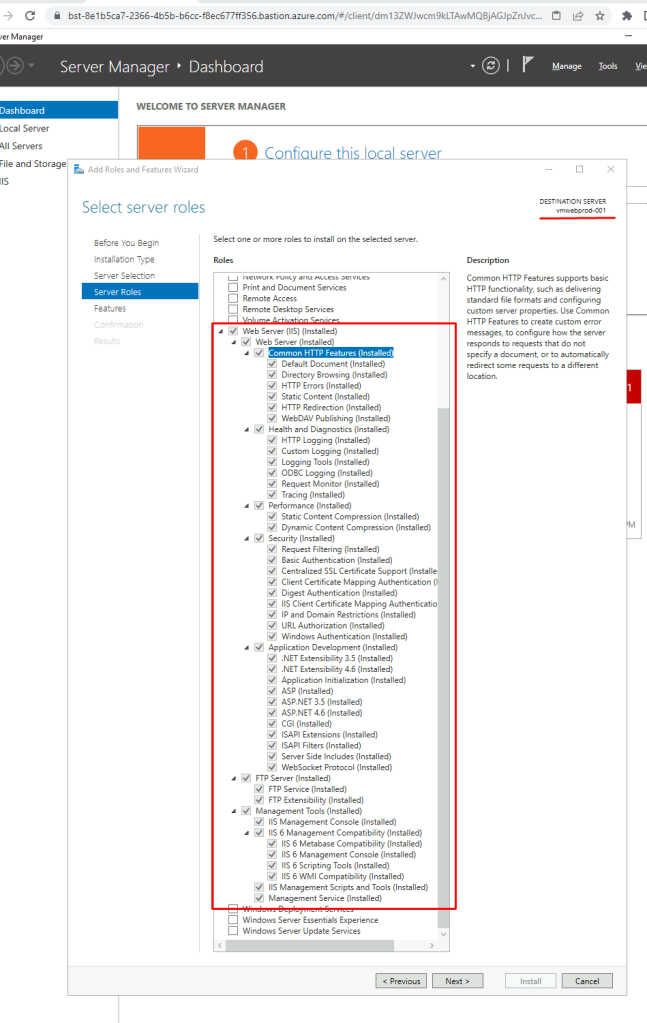

Agora vamos ver na prática o funcionamento, fiz os acessos via celular



Espero ter ajudado.
Seja Feliz!!!!!!!!!!!!!


















Você precisa fazer login para comentar.