Neste post vou demonstrar a utilização do recurso Azure “Zone DNS Private”.
Ele pode ser utilizando para substituir uma VM que seria utilizada como DNS.
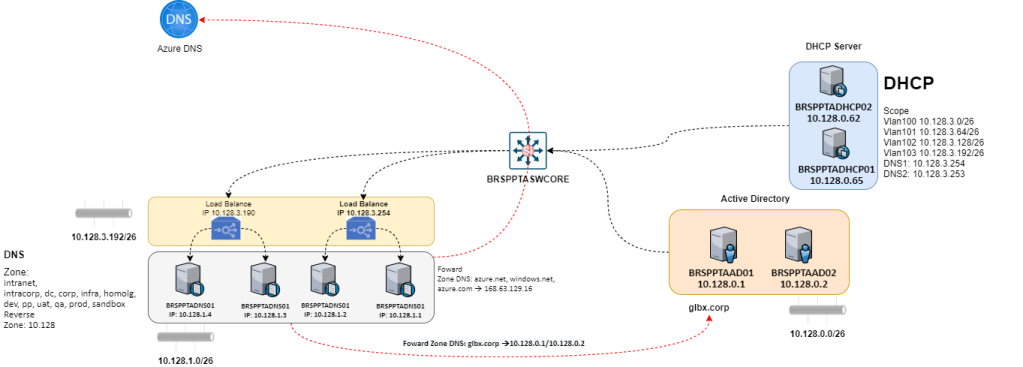
Vamos a nossa topologia:

Neste cenário teremos os seguintes objetos:
3x Virtuais Networks
1x Zona DNS Privada
Vamos a nosso script
#!/bin/bash
##Declarando variaveis
export Subscription_Name="XXXXXXXXXXX" ##Insira aqui sua subscription Azure
export RG_Name01="rg"
export RG_Name02="lab"
export RG_Name03="private"
export RG_Name04="dns"
export Location="brazilsouth"
export Environment="shared"
export RG_Name_FULL="${RG_Name01}"-"${RG_Name02}"-"${RG_Name03}"-"${RG_Name04}"-"${Environment}"-"${Location}"
##Variaveis de Objetos
export Zone_01="glbx.corp"
export LinkName01="link"
export LinkName02="zone-dns-private"
export LinkName_FULL="${Vnet_Name_FULL}"
###Declarando Variaveis Tags
export Description="Departamento"
export Value_Description="Redes/Telecom/Segurança/Infraestrutura"
export Cost_Center="Centro de Custo"
export Cost_Center_Value="Redes/Telecom/Segurança/Infraestrutura"
export Support_Description_Description="E-mail Suporte"
export Support_Description_Value="[email protected]"
###Declarando Variaveis de Rede (Vnet1)
export Vnet_Name01="vnet1"
export Vnet_Name_FULL1="${Vnet_Name01}"-"${RG_Name02}"-"${RG_Name03}"-"${RG_Name04}"-"${Environment}"-"${Location}"
export CIDR1="10.128.10.0/24"
export SubName1_01="snet"-"${RG_Name02}"-"${RG_Name03}"-"${RG_Name04}"-"${Environment}"-"${Location}"1
export SubName1_02="snet"-"${RG_Name02}"-"${RG_Name03}"-"${RG_Name04}"-"${Environment}"-"${Location}"2
export SubName1_03="snet"-"${RG_Name02}"-"${RG_Name03}"-"${RG_Name04}"-"${Environment}"-"${Location}"3
export SubName1_04="snet"-"${RG_Name02}"-"${RG_Name03}"-"${RG_Name04}"-"${Environment}"-"${Location}"4
export prefix1_01="10.128.10.0/26"
export prefix1_02="10.128.10.64/26"
export prefix1_03="10.128.10.128/26"
export prefix1_04="10.128.10.192/26"
###Declarando Variaveis de Rede (Vnet2)
export Vnet_Name02="vnet2"
export Vnet_Name_FULL2="${Vnet_Name02}"-"${RG_Name02}"-"${RG_Name03}"-"${RG_Name04}"-"${Environment}"-"${Location}"
export CIDR2="10.128.20.0/24"
export SubName2_01="snet"-"${RG_Name02}"-"${RG_Name03}"-"${RG_Name04}"-"${Environment}"-"${Location}"1
export SubName2_02="snet"-"${RG_Name02}"-"${RG_Name03}"-"${RG_Name04}"-"${Environment}"-"${Location}"2
export SubName2_03="snet"-"${RG_Name02}"-"${RG_Name03}"-"${RG_Name04}"-"${Environment}"-"${Location}"3
export SubName2_04="snet"-"${RG_Name02}"-"${RG_Name03}"-"${RG_Name04}"-"${Environment}"-"${Location}"4
export prefix2_01="10.128.20.0/26"
export prefix2_02="10.128.20.64/26"
export prefix2_03="10.128.20.128/26"
export prefix2_04="10.128.20.192/26"
###Declarando Variaveis de Rede (Vnet3)
export Vnet_Name03="vnet3"
export Vnet_Name_FULL3="${Vnet_Name03}"-"${RG_Name02}"-"${RG_Name03}"-"${RG_Name04}"-"${Environment}"-"${Location}"
export CIDR3="10.128.30.0/24"
export SubName3_01="snet"-"${RG_Name02}"-"${RG_Name03}"-"${RG_Name04}"-"${Environment}"-"${Location}"1
export SubName3_02="snet"-"${RG_Name02}"-"${RG_Name03}"-"${RG_Name04}"-"${Environment}"-"${Location}"2
export SubName3_03="snet"-"${RG_Name02}"-"${RG_Name03}"-"${RG_Name04}"-"${Environment}"-"${Location}"3
export SubName3_04="snet"-"${RG_Name02}"-"${RG_Name03}"-"${RG_Name04}"-"${Environment}"-"${Location}"4
export prefix3_01="10.128.30.0/26"
export prefix3_02="10.128.30.64/26"
export prefix3_03="10.128.30.128/26"
export prefix3_04="10.128.30.192/26"
###Variaveis de Peering
export Peering_01="peering"
export Peering_02="vnet"
export Peering_Name="${Peering_01}"-"${Peering_02}"
###Selecionar subscription
az account set --subscription "${Subscription_Name}"
##Criando RG
az group create -l "${Location}" -n "${RG_Name_FULL}" --tags "${Description}"="${Value_Description}" "${Cost_Center}"="${Cost_Center_Value}" "${Support_Description_Description}"="${Support_Description_Value}"
####Criando Virtual Network (Vnet)
az network vnet create -g "${RG_Name_FULL}" -n "${Vnet_Name_FULL1}" --address-prefix "${CIDR1}" -l "${Location}" --tags "${Description}"="${Value_Description}" "${Cost_Center}"="${Cost_Center_Value}" "${Support_Description_Description}"="${Support_Description_Value}"
az network vnet create -g "${RG_Name_FULL}" -n "${Vnet_Name_FULL2}" --address-prefix "${CIDR2}" -l "${Location}" --tags "${Description}"="${Value_Description}" "${Cost_Center}"="${Cost_Center_Value}" "${Support_Description_Description}"="${Support_Description_Value}"
az network vnet create -g "${RG_Name_FULL}" -n "${Vnet_Name_FULL3}" --address-prefix "${CIDR3}" -l "${Location}" --tags "${Description}"="${Value_Description}" "${Cost_Center}"="${Cost_Center_Value}" "${Support_Description_Description}"="${Support_Description_Value}"
####Criando Subnet
az network vnet subnet create -g "${RG_Name_FULL}" --vnet-name "${Vnet_Name_FULL1}" -n "${SubName1_01}" --address-prefixes "${prefix1_01}"
az network vnet subnet create -g "${RG_Name_FULL}" --vnet-name "${Vnet_Name_FULL1}" -n "${SubName1_02}" --address-prefixes "${prefix1_02}"
az network vnet subnet create -g "${RG_Name_FULL}" --vnet-name "${Vnet_Name_FULL1}" -n "${SubName1_03}" --address-prefixes "${prefix1_03}"
az network vnet subnet create -g "${RG_Name_FULL}" --vnet-name "${Vnet_Name_FULL1}" -n "${SubName1_04}" --address-prefixes "${prefix1_04}"
az network vnet subnet create -g "${RG_Name_FULL}" --vnet-name "${Vnet_Name_FULL2}" -n "${SubName2_01}" --address-prefixes "${prefix2_01}"
az network vnet subnet create -g "${RG_Name_FULL}" --vnet-name "${Vnet_Name_FULL2}" -n "${SubName2_02}" --address-prefixes "${prefix2_02}"
az network vnet subnet create -g "${RG_Name_FULL}" --vnet-name "${Vnet_Name_FULL2}" -n "${SubName2_03}" --address-prefixes "${prefix2_03}"
az network vnet subnet create -g "${RG_Name_FULL}" --vnet-name "${Vnet_Name_FULL2}" -n "${SubName2_04}" --address-prefixes "${prefix2_04}"
az network vnet subnet create -g "${RG_Name_FULL}" --vnet-name "${Vnet_Name_FULL3}" -n "${SubName3_01}" --address-prefixes "${prefix3_01}"
az network vnet subnet create -g "${RG_Name_FULL}" --vnet-name "${Vnet_Name_FULL3}" -n "${SubName3_02}" --address-prefixes "${prefix3_02}"
az network vnet subnet create -g "${RG_Name_FULL}" --vnet-name "${Vnet_Name_FULL3}" -n "${SubName3_03}" --address-prefixes "${prefix3_03}"
az network vnet subnet create -g "${RG_Name_FULL}" --vnet-name "${Vnet_Name_FULL3}" -n "${SubName3_04}" --address-prefixes "${prefix3_04}"
#Criando Peering entre as Vnets
##Peering entre vnet1 e vnet2
az network vnet peering create -g "${RG_Name_FULL}" -n "${Peering_Name}"-"${Vnet_Name_FULL2}" --vnet-name "${Vnet_Name_FULL1}" --remote-vnet "${Vnet_Name_FULL2}" --allow-vnet-access --allow-forwarded-traffic --allow-gateway-transit --allow-vnet-access
az network vnet peering create -g "${RG_Name_FULL}" -n "${Peering_Name}"-"${Vnet_Name_FULL1}" --vnet-name "${Vnet_Name_FULL2}" --remote-vnet "${Vnet_Name_FULL1}" --allow-vnet-access --allow-forwarded-traffic --allow-gateway-transit --allow-vnet-access
##Peering entre vnet1 e vnet3
az network vnet peering create -g "${RG_Name_FULL}" -n "${Peering_Name}"-"${Vnet_Name_FULL3}" --vnet-name "${Vnet_Name_FULL1}" --remote-vnet "${Vnet_Name_FULL3}" --allow-vnet-access --allow-forwarded-traffic --allow-gateway-transit --allow-vnet-access
az network vnet peering create -g "${RG_Name_FULL}" -n "${Peering_Name}"-"${Vnet_Name_FULL1}" --vnet-name "${Vnet_Name_FULL3}" --remote-vnet "${Vnet_Name_FULL1}" --allow-vnet-access --allow-forwarded-traffic --allow-gateway-transit --allow-vnet-access
##Peering entre vnet2 e vnet3
az network vnet peering create -g "${RG_Name_FULL}" -n "${Peering_Name}"-"${Vnet_Name_FULL3}" --vnet-name "${Vnet_Name_FULL3}" --remote-vnet "${Vnet_Name_FULL2}" --allow-vnet-access --allow-forwarded-traffic --allow-gateway-transit --allow-vnet-access
az network vnet peering create -g "${RG_Name_FULL}" -n "${Peering_Name}"-"${Vnet_Name_FULL2}" --vnet-name "${Vnet_Name_FULL2}" --remote-vnet "${Vnet_Name_FULL3}" --allow-vnet-access --allow-forwarded-traffic --allow-gateway-transit --allow-vnet-access
###Criando Zone DNS Privada
az network private-dns zone create -g "${RG_Name_FULL}" -n "${Zone_01}" --tags "${Description}"="${Value_Description}" "${Cost_Center}"="${Cost_Center_Value}" "${Support_Description_Description}"="${Support_Description_Value}"
###criando entradas "." apontando para nossos ADs (Active Directory)
az network private-dns record-set a add-record -g "${RG_Name_FULL}" -z "${Zone_01}" -n "@" -a 10.128.10.4
az network private-dns record-set a add-record -g "${RG_Name_FULL}" -z "${Zone_01}" -n "@" -a 10.128.20.4
az network private-dns record-set a add-record -g "${RG_Name_FULL}" -z "${Zone_01}" -n "@" -a 10.128.30.4
az network private-dns record-set a add-record -g "${RG_Name_FULL}" -z "${Zone_01}" -n "VMAD01" -a 10.128.10.4
az network private-dns record-set a add-record -g "${RG_Name_FULL}" -z "${Zone_01}" -n "VMAD02" -a 10.128.20.4
az network private-dns record-set a add-record -g "${RG_Name_FULL}" -z "${Zone_01}" -n "VMAD03" -a 10.128.30.4
###Variavels para pegar ID da Vnet para vincular com Zone Private DNS Azure
SUBNET_ID001=$(az network vnet show -n "${Vnet_Name_FULL1}" -g "${RG_Name_FULL}" --query id --output tsv)
SUBNET_ID002=$(az network vnet show -n "${Vnet_Name_FULL2}" -g "${RG_Name_FULL}" --query id --output tsv)
SUBNET_ID003=$(az network vnet show -n "${Vnet_Name_FULL3}" -g "${RG_Name_FULL}" --query id --output tsv)
###Criando link de zona dns privada com vnet
az network private-dns link vnet create -g "${RG_Name_FULL}" -n "${LinkName_FULL}"-"${Vnet_Name_FULL1}" -z "${Zone_01}" -v $SUBNET_ID001 -e False
az network private-dns link vnet create -g "${RG_Name_FULL}" -n "${LinkName_FULL}"-"${Vnet_Name_FULL2}" -z "${Zone_01}" -v $SUBNET_ID002 -e False
az network private-dns link vnet create -g "${RG_Name_FULL}" -n "${LinkName_FULL}"-"${Vnet_Name_FULL3}" -z "${Zone_01}" -v $SUBNET_ID003 -e False
###Criando entradas em zona dns privada
az network private-dns record-set a add-record -g "${RG_Name_FULL}" -z "${Zone_01}" -n "intranet" -a 10.128.10.10
az network private-dns record-set a add-record -g "${RG_Name_FULL}" -z "${Zone_01}" -n "site6" -a 10.128.20.10
az network private-dns record-set a add-record -g "${RG_Name_FULL}" -z "${Zone_01}" -n "portalrh" -a 10.128.30.10
Vamos a expliação
Zona de DNS Privada
Neste objeto nos teremos a seguinte zona privada “glbx.corp” nosso fqdn do nosso dominio
Virtual Networks (Não alteramos o DNS da Vnet)
Neste teremos 3x Virtuais Network em nosso ambientes
vnet1-lab-private-dns-shared-brazilsouth = 10.128.10.0/24
vnet2-lab-private-dns-shared-brazilsouth = 10.128.20.0/24
vnet3-lab-private-dns-shared-brazilsouth = 10.128.30.0/24
Dentro de nossa zona “glbx.corp” teremos as seguintes entradas
@ 10.128.10.4 (AD)
@ 10.128.20.4 (AD)
@ 10.128.30.4 (AD)
| Nome | Tipo | TTL | Valor |
| @ | A | 300 | 10.128.10.4 |
| @ | A | 300 | 10.128.20.4 |
| @ | A | 300 | 10.128.30.4 |
| intranet | A | 3600 | 10.128.10.10 |
| portalrh | A | 3600 | 10.128.20.10 |
| site6 | A | 3600 | 10.128.30.10 |
Teremos “Peering” entre as “Vnet” (Não utilizei um firewall para ficar mais facil a explicação), o peering server para as vnets se falarem (desta forma, teram que fazer a segurança vai NSG).
Em cada Vnet temos algumas Virtuais Machines (não esta no desenho)
VMAD01 10.128.10.4
VMAD02 10.128.20.4
VMAD03 10.128.30.4
VMINTRANET 10.128.10.10
VMRH01 10.128.20.10
VMSITE6 10.128.30.10
Pronto, com nosso ambiente criada nossas VMs/Endpoint conseguem resolver nomes utilizando o DNS do Azure com nossa Zona de DNS Privada, veja como ficou:
Veja que resolve nosso dominio para os servidores certos

Veja que resolve as entradas criadas

***Para que na sua infraestrutura funcione a utlização de “Azure DNS Private” você não pode esquecer de criar os Links da Zona Privada com sua Vnet.
Links de referencias
https://docs.microsoft.com/en-us/azure/dns/private-dns-overview


Você precisa fazer login para comentar.